
There are, by some estimates, more smart phones on this planet than human beings to use them. People who have never used a desktop computer use smart phones and other mobile devices every day and have much of their lives tethered to them—maybe more than they should.
As a result, cyber-grifters have shifted their focus from sending emails to gullible personal computer users (pretending to be Nigerian princes in need of banking assistance) and have instead set their sights on the easier target of cell phone users. Criminals are using smartphone apps and text messages to lure vulnerable people into traps—some with purely financial consequences, and some that put the victims in actual physical jeopardy.
I recently outlined some ways to apply a bit of armor to our digital lives, but recent trends in online scams have underscored just how easily smartphones and their apps can be turned against their users. It's worth reviewing these worst-case scenarios to help others spot and avoid them—and we aren't just talking about helping older users with this. This stuff affects everyone.

I've personally been contacted by a variety of people who've been victims of mobile-focused scams and by people who've found themselves exposed and targeted via unexpected vulnerabilities created by interactions with mobile apps. For some, these experiences have shattered their sense of privacy and security, and for others, these scams have cost them thousands (or tens of thousands) of dollars. In light of this, it's worth arming yourself and your family with information and a whole lot of skepticism.
Targeted SMS phishing
The last two years have seen a tremendous uptick in text message phishing scams that target personal data—especially website credentials and credit card data. Sometimes called "smishing," SMS phishing messages usually carry some call to action that motivates the recipient to click on a link—a link that often leads to a web page that is intended to steal usernames and passwords (or do something worse). These spam text messages are nothing new, but they are becoming increasingly more targeted.
In 2020, the FTC reported that US consumers lost $86 million as a result of scam texts, and the FCC went as far as to issue a warning about COVID-19 text scams. Sure, sure, you're smart and you would never give up your personal data to a sketchy text message. But what if the text mentioned your name, along with enough correct information to make you just the slightest bit concerned? Like a text message purportedly from your bank, giving your name, asking you to log in to confirm or contest a $500 charge on your credit card at Walmart?

That's the kind of message I recently received. If I had not read the message carefully or noticed that it had come from a spoofed phone number that was not connected to my bank or failed to remember that I had never consented to any communications with my bank via text messages, I might have clicked.
Instead, I went into my bank's mobile app and found a notice on the login page that customers were experiencing fraud attempts through text messages. I took the link to my computer and pulled down the page using wget. The link pointed at a Google App Engine page that contained a link in an IFRAME element to a Russian website—one that attempted to emulate the bank's website login.
SMS scams like these are made easier by the rafts of public data exposure and the aggregation of personal details by marketers. This kind of data is all too often collected in databases that get leaked or hacked. Scammers can target large numbers of customers of a specific brand just by connecting their relationship to a company with their phone numbers. I don't have good scientific data on the prevalence of targeted "smishing," but a random sampling of family and friends indicates it's not just a passing problem: in some cases it constitutes half of the daily SMS messages they receive.
Most of it is the equivalent of pop-up web ads. Some of the targeted SMS messages I've seen have purported to be from common services—like Netflix, for example:
Netflix: [Name], please update your membership with us to continue watching. [very sketchy URL]
The sketchy link led to a site claiming my last payment had been declined, and I had 48 hours to re-activate my account.
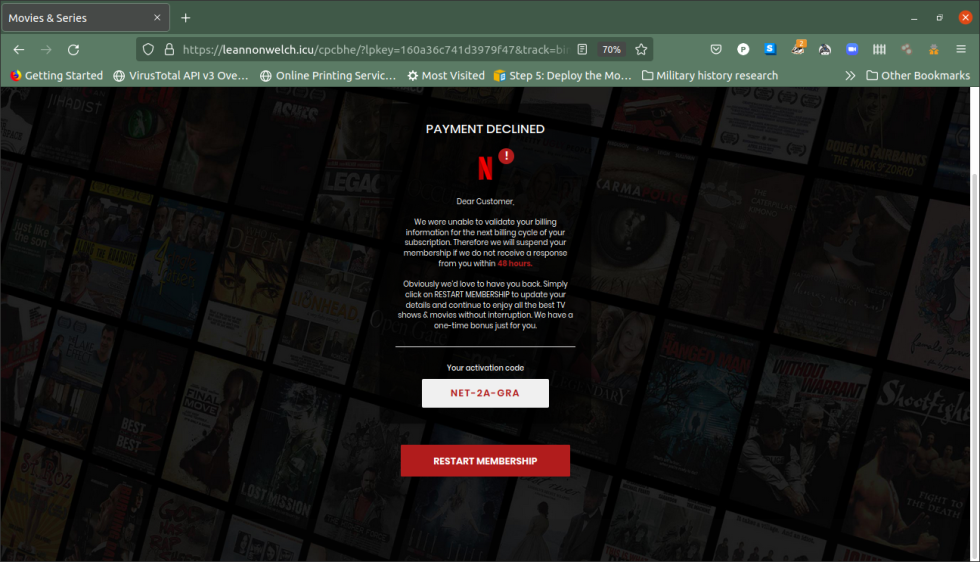
Clicking on that link funnels you into a series of page forwards powered by a "tracker" site configured to filter out suspicious clicks (like ones from PC browsers), sending only mobile browsers to the intended destination—in this case, a Netflix look-alike service that tries to get you to enroll as a member. Your IP address is one of the arguments passed to the final URL in order to keep out undesirable ranges of "customers."
This is light scamming, to be sure. But the same tracker sites are used by a wide range of scams, including SMS and mobile browser pop-up "fake alert" scams. These types of scams often feature an urgent call to action. Another frequent angle is claiming that the recipient's IP address "is being tracked due to viruses," with a link that leads to an app store page—usually some kind of questionable virtual private network app that may in fact do nothing other than collect "in-app payments" through the Apple or Google app stores for a service that doesn't work. Or the service does work—but not in ways that the device owner would like.
Fleece apps and fake apps
Despite efforts by big companies to check the security of applications before they're offered for download on app stores, scammer developers regularly manage to slip nasty things into the iOS and Android marketplaces—nasty cheap or "free" apps of limited (or nonexistent) usefulness that deceive users into paying large amounts of money.

Often, these applications are presented as free but feature in-app payments—including subscription fees that automatically kick in after a very short "trial period" that may not be fully transparent to the user. Often referred to as "fleeceware," apps like this can charge whatever the developer wants on a repeating basis. And they may even continue to generate charges after a user has uninstalled the application.
To be sure that you're not being charged for apps you've removed, you have to go check your list of subscriptions (this works differently on iOS and Google Play)—and remove any that you aren't using.
Occasionally, malicious applications manage to slip past app store screening. When caught, the developer accounts associated with the apps are usually suspended—and the apps are removed from the stores and (usually) from devices they've been installed on. But the developers of these apps often just roll over to another developer account or use other ways to get their apps in front of users.
I tracked a campaign of pop-up ads that drove smart phone users to "security" applications on both app stores, using fake alert pages resembling mobile operating system alerts that warned of virus infections on devices. When the ads detected an iOS device, they ended by opening the page of a VPN application from a developer in Belarus that charged $10 a week for service. The app store listing was replete with (likely fake) 4-star reviews, along with a few from actual customers who discovered they had been scammed.
The app itself worked, sort of—it directed all users' Internet traffic through a server in Belarus, allowing for man-in-the-middle attacks and the collection of enormous amounts of user data.
Sure, a sophisticated device user would know that these apps are fraudulent and spot them right away, right? Possibly—but how many iOS and Android users have that level of sophistication?
Pigs to the slaughter
There is also a world of truly malicious applications that exist on the fringes of Apple's and Google's ecosystems. These apps use fake app stores and often require significant amounts of social engineering to get victims to install them (unless the target is someone already using a "cracked" device to intentionally get access to alternative app stores).
One type of scam that leans heavily on social engineering has become known in China as "杀猪盘"—sha zhu pan, or "pig butchering" in English. Instead of targeting older people, this long play leverages personal relationships and cryptocurrency greed to go after younger digital natives.

A common narrative of these scams goes like this: someone reaches out on a dating app or some other app that drives social connections—like HelloTalk, an app that connects people trying to learn languages with native speakers. After an initial connection, the scammer tries to move the conversation to WhatsApp or WeChat or to some other platform-independent messaging app, making some excuse as to why. (Frequently, the scammer's account on the original app platform will then go dark afterward or disappear entirely, and the scammer will blame it on an account issue or a hack or some other convenient excuse.)
Then the scammer messages the target every day. Pictures of food. Pictures of places they've gone. Pictures of themselves. (These may be real or stolen from someone else's social media.) They'll try to at least gain confidence—and, often, they'll push for a romantic connection. And then they'll start talking about how much money they're making on Bitcoin.
Many otherwise perfectly sane people, ages 18 and up, go without smelling the scam. They then get lured into putting some money in an account, with a "loan" from the scammer to sweeten the pot. This happens through a fake crypto trading app, with a design stolen from a legitimate service (usually in Asia), installed from a webpage designed to look like the Apple or Google Play app store. For iOS applications, this is usually a front-end to an ad-hoc or enterprise developer app deployment scheme that requires the installation of a configuration profile—one that might actually link your device to the scammer's mobile device management system and allow the remote installation of apps to your phone. Other scammers bypass the whole profile nastiness by using a mobile webpage.
Pay no attention to any of the alerts that pop up during this process, the scammer will assure you. This is all just to make sure the trading app is secure. And the assurances usually work—how often do most folks blindly click through alerts, especially when they have reason to believe that the alerts are extraneous?
For some time after this, everything might seem on the up and up. The app might even let you take some money out. But then that "friend" will encourage you to deposit more and more—by sending payments to a specified Bitcoin wallet, perhaps—and then suddenly you can't get your money out at all.
These scams rake in millions. One victim claimed to have lost over $60,000. "Pig butchering" scams have become so commonplace that they've led to a booming secondary support market for fake dating profiles and other essential content for luring victims and convincing them that they're legit.
Safety takeaways
Scammers are most successful when they target people at their most vulnerable—by causing fear, leveraging loneliness, playing to greed, or weaponizing shame. That's how Internet scams have always worked. And the scammers have followed the money, from spam emails to dating sites to Yahoo Instant Messenger to Twitter and Facebook, and now to the green pastures of mobile apps.
To protect those you know who might be vulnerable to any of the tactics I've mentioned here, provide them with these rules of thumb:
- Your bank will not text you about your account unless you have specifically signed up for text alerts.
- The same goes for virtually every other service you use, including the IRS, the Social Security Administration, and any other organization with your personal identifying information.
- If you get something that looks like a text alert from one of these institutions, either call them or log in to the website or app you normally use to interact with them. Don't click any links from a text message. Verify the message through a different channel, like the institution's phone app or its website.
- Read the terms for applications carefully before installing them. Look for subscription requirements that seem unreasonable or out of place for the service. Check your subscriptions after you remove apps to ensure you're not still paying for them.
- Be sure to do some due diligence on people who contact you through mobile apps. Reverse-image searching is a good way to find reused pictures stolen from other profiles, though it's not as effective as it once was because of artificial intelligence tools like This Person Does Not Exist—scammers can create profiles using images of totally fabricated individuals, but it takes some effort to keep that illusion going.
- Only install applications from within the app store of your platform, and never follow a link someone provided to go to an app installation page. Instead, search for it by name in the store, look for a number of downloads, and check the developer name. If you're ever asked by an app to install a configuration profile and it isn't for a VPN, this is a huge red flag—check to make sure you're actually installing it from the app store.
And don't ever take investment advice from some rando on the Internet—especially if they claim to be Elon Musk. One Elon is more than enough.
https://ift.tt/3cfMjIY
Technology
Bagikan Berita Ini














0 Response to "Securing your digital life, part three: How smartphones make us vulnerable - Ars Technica"
Post a Comment